Human Rights Policy

Ethical Corporate Management Best Practice Principles



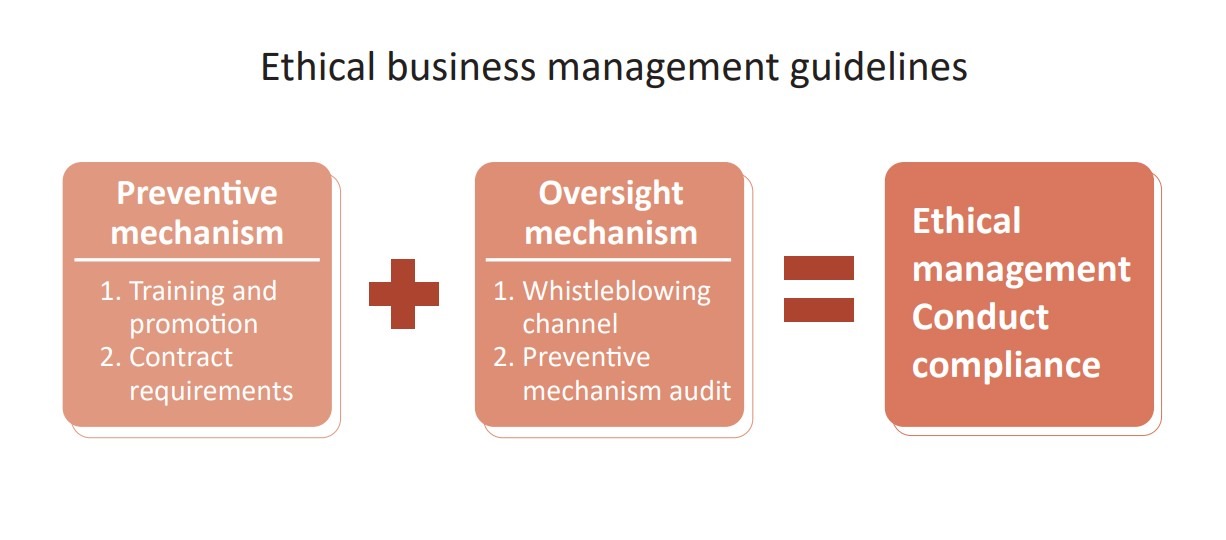
Ethical Management
Corum's core values are inspired by legal compliance and integrity, and the Company engages in business in the spirit of integrity and legal compliance. To ensure the implementa-tion of ethical business philosophy within the Company, we have always attached great impor-tance to our colleagues' ethics; the HR Department promotes the Company's internal integrityregulations to the new employees when they are reporting for duty to cultivate their integrityawareness. At the same time, the management is required to lead by example and comply withthe principle of integrity in an effort to foster the Company's ethical culture.
Corum's HR Department is responsible for promoting the principle of ethical management.The "Corum Ethical Corporate Management Best Practice" was formulated, and a correspond-ing contact person was appointed to let stakeholders express their opinions. If our colleagues have questions about the Company's integrity internal regulations, besides searching forrelevant information on the official website, they can also consult the HR Department viadiverse channels such as email or telephone.
Meanwhile, we have set up diverse whistleblowing channels, allowing our stakeholders tofile complaints via the Company website or the HR Department's email (anonymous and named). The facts and evidence of the report will be clarified, and the Company will take appro-priate disciplinary measures depending on the seriousness of the circumstances. The content of the report and the whistleblower's identity will be kept confidential, and the Company will protect the whistleblower and employees partaking in the investigation process to prevent unfair retaliation or treatment.
In regards to business interaction, Corum's colleagues should explain the Company's ethicalmanagement policy and relevant regulations to the other party during the transaction process.Moreover, they may not provide, promise, demand, or accept any form of improper benefits either directly or indirectly. At the same time, transactions with unethical agents, suppliers,customers, or other business partners should be avoided. If the business or cooperativepartners are found to exhibit unethical conduct, evaluations should be conducted to determine whether to blacklist them to materialize the Company's ethical management policy. Further-more, we have included Corum's ethical management policy into both parties' contract terms,stipulating the relevant regulations and requirements in the contract. Should any party engage in business activities suspicious of unethical conduct, the other party reserves the right to unconditionally terminate or rescind the contract at any time.
process, the HR Department will progressively devise online ethical training for in-service colleagues in the future, where senior executives will convey the importance of the Company's ethical culture to the colleagues during meetings. Meanwhile, the HR Department should implement, check, and evaluate the effectiveness of the preventive measures in place with the management, as well as report the execution outcome of the compliance of various business processes to the Board of Directors every year. In 2021, no ethics-related complaints were received internally or externally.
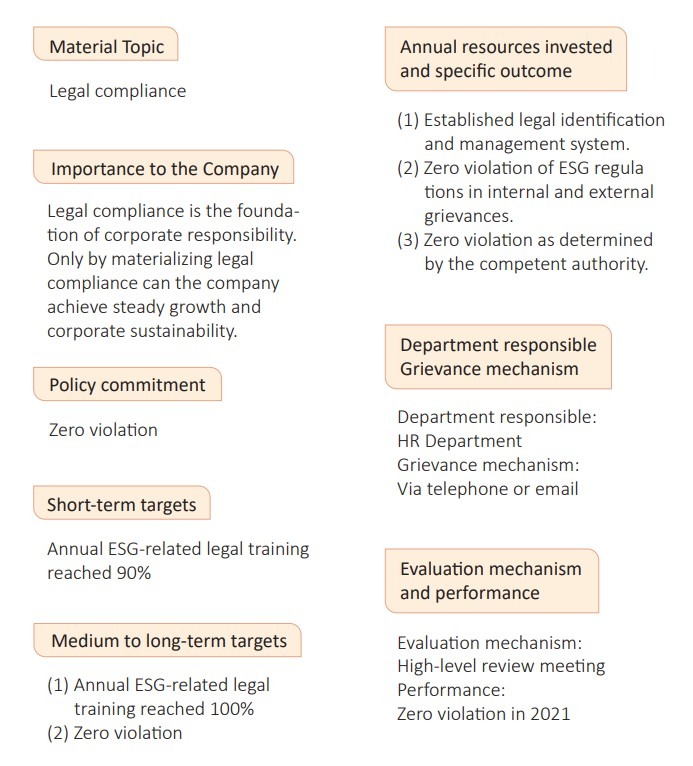
Legal compliance
Corum communicates the Company's internal ethical regulations to our new employees when they are reporting for duty. Due to the wide range of legal regulations, different depart-ments will implement internal and external training for the colleagues after obtaining informa-tion on revisions to the law through interaction with government agencies or media reports in order to ensure the Company's operations comply with various regulations.
(1) In terms of corporate governance, Corum continues to follow the Corporate Governance Best-Practice Principles in a bid to increase colleagues' legal compliance awareness.
(2) Concerning personnel management, internal meetings are held to promote the Company's core values of ethics and integrity. Through the formulation of a series of regulations, imple mentation of a self-review system, and establishment of a whistleblowing channel and whistleblower protection mechanism, we have created a comprehensive legal compliance firewall. The management leads by example, demanding our colleagues to make sure that their business conducts comply with the law or the Company's policies and internal regulations. The compliance status is examined through annual review meetings, and compliance guidelines are formulated for our colleagues, demanding them to comply with the "Human Rights Policy of CORUM and CORUM Ethical Corporate Management Best Practice Principles", irrespective of their position, rank, and location. The content includes work environment guidelines, equal opportunity, confidentiality clause, prohibition of part-time work, avoidance of conflicts of interest, prohibition of giving or receiving gifts, and compliance with business etiquette. Improve our corporate image through measures such as respecting employees and customers, whistleblower protection and immunity, etc. to ensure the Company's sustainable management and development. To prevent the Company from being punished for violating fair competition and antitrust laws, we have especially stipulated relevant codes of conduct, which should be complied with by the Company's management and employees while conducting business activities to lower the risk of breaking the law. The abovementioned measures were implemented for the sake of engaging in industrial compe tition by following the principle of integrity and fairness, thereby fostering a corporate culture of legal compliance and establishing a trustworthy, respected reputation for the Company.
(3) In terms of personnel training, to elevate our colleagues' professional ethics and legal compliance awareness, we have created internal regulations in accordance with the law, where the HR Department and other responsible departments work together to provide colleagues from different departments and ranks with relevant legal training. For instance, we provide colleagues with corresponding training based on their respective responsibilities including orientation training, physical courses, cross-unit promotion, and external training. Moreover,legal compliance guidelines are announced on posters in the Chiayi factory and on the Company website to allow our colleagues to stay in touch with the latest regulations at any time.
(4) Regarding occupational safety and health, Corum has introduced the ISO 14001 environmen tal management system and ISO 45001 occupational safety and health management system,and we have formulated the oversight, audit, and performance management regulations to ensure that the Company complies with environmental protection and occupational safety requirements during the product manufacturing process. Through an effective, circular operational environment and occupational safety management system, we can detect potential problems and take the appropriate management and preventive actions to protect the Company from damages.

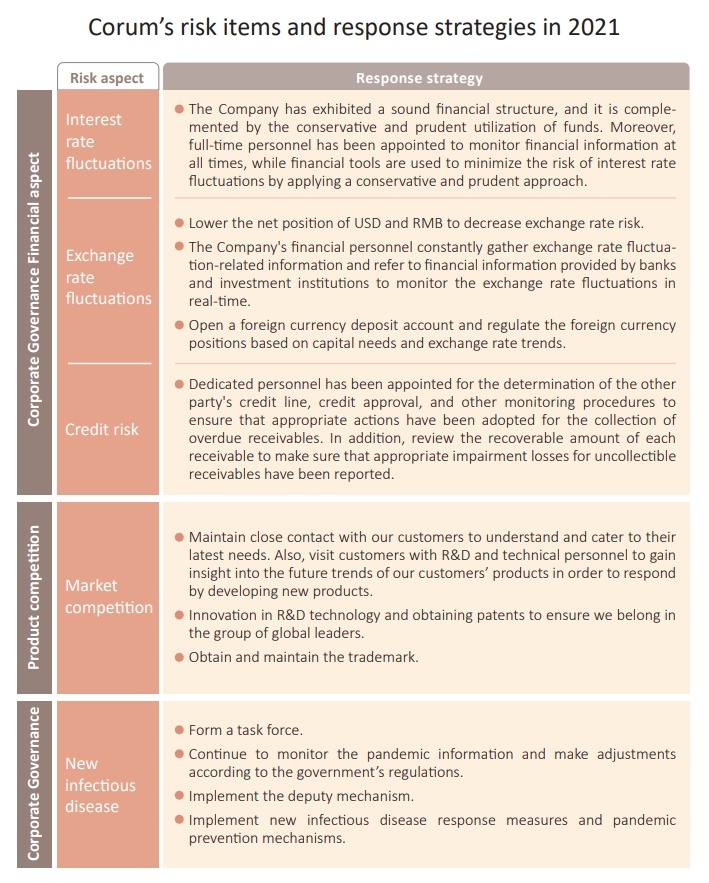
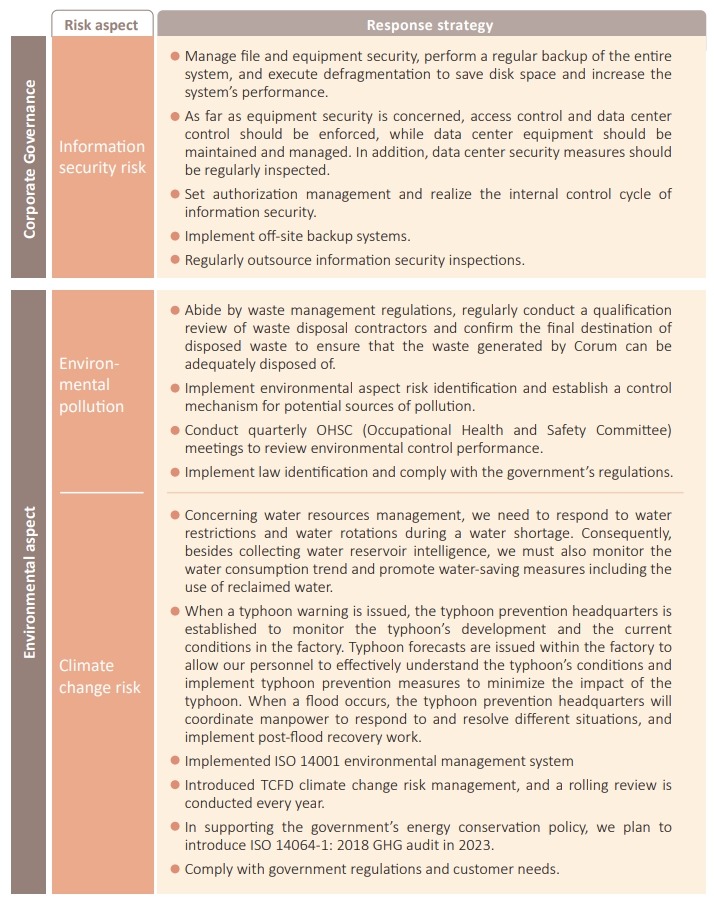
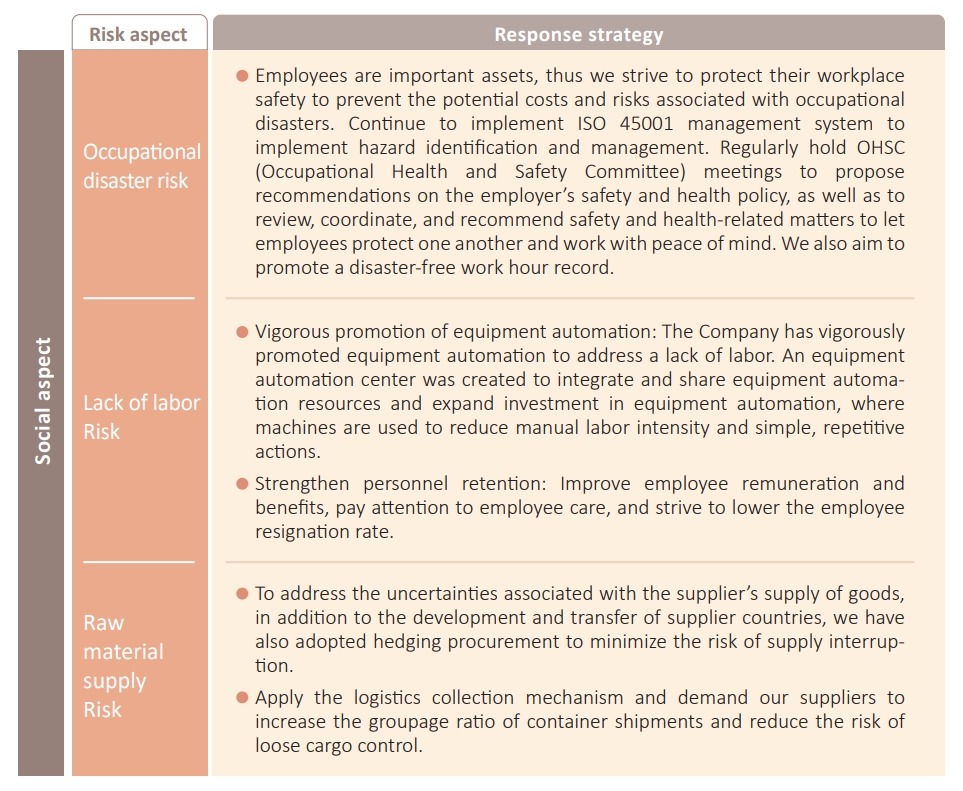
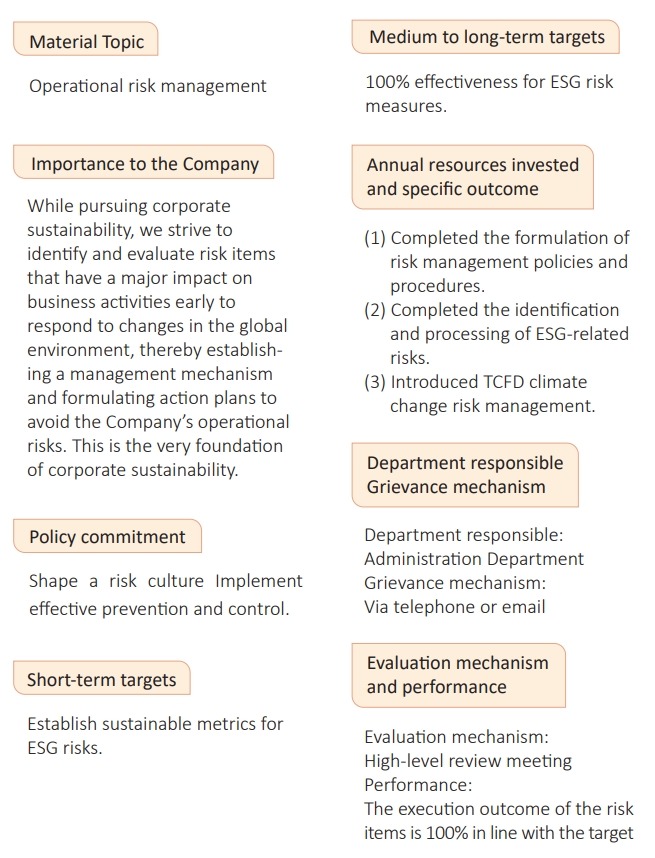
Total Risk Management

planning and implementing risk manage-ment-related activities. Risk management encompasses corporate governance, environmental,and social aspects. Focusing on various responsible departments, we have launched relevant risk evaluation operations to ensure the Company's sustainability goals are achieved by evaluat-ing the risk probability and the level of its impact on the Company, as well as responding to specific high-risk items.
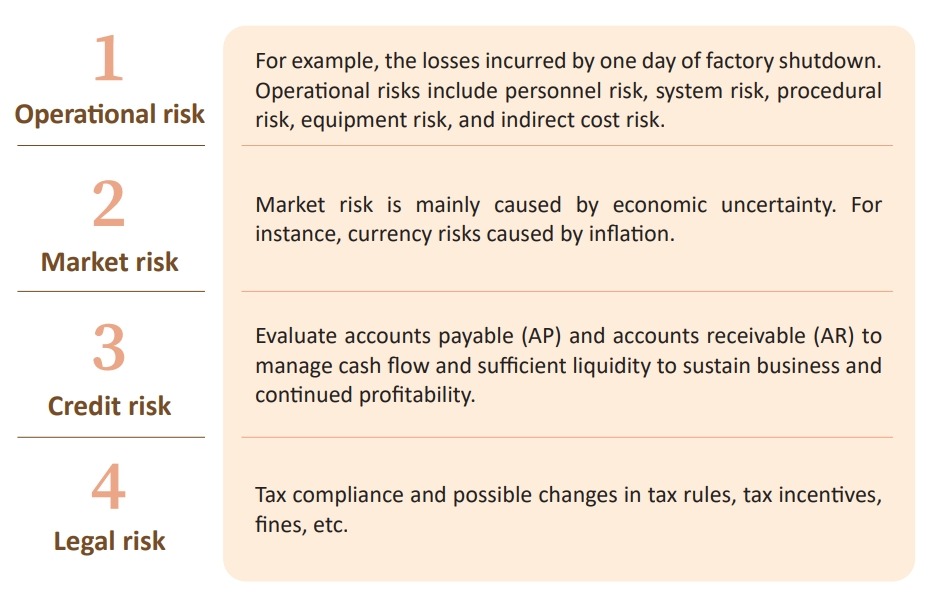
Currently, the material financial impact is defined by Corum's Finance Center based on calculations of four major types of financial risks:

COVID-19 pandemic prevention measures
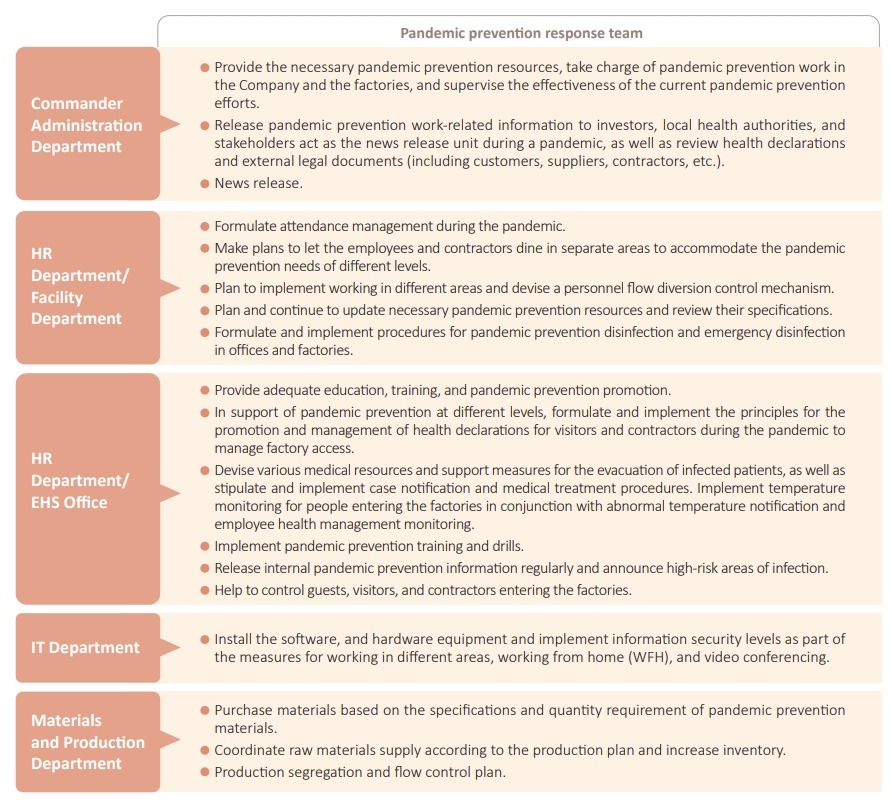
Besides forming a pandemic prevention response team, Corum has also implemented the following:
1.Request various units to reinforce environmental cleaning and disinfection management.
2.Request the employees to wear masks, take body temperatures every day, and conduct self-health management. If abnormal health conditions are discovered, the Company will immediately try to understand, monitor the situation, and provide relevant assistance in pandemic prevention.
3.To minimize employee interaction, elevator traffic is diverted, and thebuilding's security door only allows people to leave, no entry is permitted. Visitors or people exhibiting abnormal health conditions are prohibited from entering the building.
4.Meetings or client visits are carried out online to decrease cluster infection.
5.Monitor the Central Epidemic Command Center's latest directives and respond swiftly.
6.Depending on the needs of various units, relevant computer files and reports are backed up by scanning, external hard drives, or flash drives so that colleagues working from home may continue their work and ensure normal business operation.
7.Various units form LINE groups, save cell phone numbers, emails, or other communication information, allowing personnel to contact at any time, thereby decreasing the risk of cross-infection due to contact.
8.Employees who must work from home for a certain reason or are quarantined at home should refer to the information management regulations if they need to connect to the Company's intranet via VPN.
Information Security Management
With the high level of development in the information age, the Company isvulnerable to unpredictable security risks while enjoying the benefits of conve-nience. In serious cases, the Company's information network and business may be interrupted, causing enormous damage to the Company and the stakeholders.The Company's highest-ranking executive is the IT executive, who is in charge of planning and promoting the information security measures of the headquarters and factories. An "information security team" is formed consisting of executives from IT and other units. It must engage in security prevention, crisis handling, and audit operations.
Information security policy
Abide by information security-related laws and provide adequate protection measures for the Company's information asset to ensure its confidentiality,integrity, and availability, acting as the highest guiding principle for the Compa-ny's information security management and operations.
● Regularly assess potential hazards' impact on the Company's information assets, formulate contingency and recovery plans for important information assets and key services. This is to make sure the ongoing operation of the Company.
● Encourage our employees to implement information security protection,establish relevant regulations and information security responsibilities,concepts, and conducts.
● Contractors, customers, or third-party personnel that have used or linked to the Company's information environment must adhere to the Company's information security policy and related regulations.
Information security management mechanism and solution
● User authorization management: The user must grant different authorizations according to different security levels.
● Operating system user authorization security management: Install the operating system in accordance with the Company's regulations and join the Company domain for centralized management. The operating system must receive regular security updates, while antivirus software must be installed on the Company's servers and computers. Furthermore, updates,scan engine, and virus codes are downloaded automatically every day. Measures for regularly renewing the user password.
● Application software security management: Besides installing the application software, tool software, and software suites needed for IT operations, installation of other special software requires separate applications and approval before it can be installed.
● Set up a screening mechanism for prohibited software and URLs in the firewall settings to deny access to prevent affecting network quality and security.
● Network communication security management: External VPN (remote) access and internal access (file transfer (FTP), instant messaging, special connection (HTTPS), and other network applications) must be reviewed by the information unit and approved by the executive in charge before access is granted.
● Application system security management: The information unit must restrict the access and update of the source code to authorized personnel, and set different program execution authorizations for different users based on the business needs.
● Backup management: System disaster recovery and database backup management-related measures are in place.
● Asset management: Conduct asset serial number management and regular inventory of equip- ment and personal computers in the data center.
● The online training method is applied to educate users on the security mechanism of operating system configuration and operation. The source and infection method of current viruses (Trojan horses, backdoors, worms, etc.) are explained to enhance the users' knowledge of security protection.

Human Rights Policy


Ethical Corporate Management Best Practice Principles




Ethical Management

Corum's core values are inspired by legal compliance and integrity, and the Company engages in business in the spirit of integrity and legal compliance. To ensure the implementa-tion of ethical business philosophy within the Company, we have always attached great impor-tance to our colleagues' ethics; the HR Department promotes the Company's internal integrityregulations to the new employees when they are reporting for duty to cultivate their integrityawareness. At the same time, the management is required to lead by example and comply withthe principle of integrity in an effort to foster the Company's ethical culture.
Corum's HR Department is responsible for promoting the principle of ethical management.The "Corum Ethical Corporate Management Best Practice" was formulated, and a correspond-ing contact person was appointed to let stakeholders express their opinions. If our colleagues have questions about the Company's integrity internal regulations, besides searching forrelevant information on the official website, they can also consult the HR Department viadiverse channels such as email or telephone.
Meanwhile, we have set up diverse whistleblowing channels, allowing our stakeholders tofile complaints via the Company website or the HR Department's email (anonymous and named). The facts and evidence of the report will be clarified, and the Company will take appro-priate disciplinary measures depending on the seriousness of the circumstances. The content of the report and the whistleblower's identity will be kept confidential, and the Company will protect the whistleblower and employees partaking in the investigation process to prevent unfair retaliation or treatment.
In regards to business interaction, Corum's colleagues should explain the Company's ethicalmanagement policy and relevant regulations to the other party during the transaction process.Moreover, they may not provide, promise, demand, or accept any form of improper benefits either directly or indirectly. At the same time, transactions with unethical agents, suppliers,customers, or other business partners should be avoided. If the business or cooperativepartners are found to exhibit unethical conduct, evaluations should be conducted to determine whether to blacklist them to materialize the Company's ethical management policy. Further-more, we have included Corum's ethical management policy into both parties' contract terms,stipulating the relevant regulations and requirements in the contract. Should any party engage in business activities suspicious of unethical conduct, the other party reserves the right to unconditionally terminate or rescind the contract at any time.
process, the HR Department will progressively devise online ethical training for in-service colleagues in the future, where senior executives will convey the importance of the Company's ethical culture to the colleagues during meetings. Meanwhile, the HR Department should implement, check, and evaluate the effectiveness of the preventive measures in place with the management, as well as report the execution outcome of the compliance of various business processes to the Board of Directors every year. In 2021, no ethics-related complaints were received internally or externally.

Legal compliance
Corum communicates the Company's internal ethical regulations to our new employees when they are reporting for duty. Due to the wide range of legal regulations, different depart-ments will implement internal and external training for the colleagues after obtaining informa-tion on revisions to the law through interaction with government agencies or media reports in order to ensure the Company's operations comply with various regulations.
(1) In terms of corporate governance, Corum continues to follow the Corporate Governance Best-Practice Principles in a bid to increase colleagues' legal compliance awareness.
(2) Concerning personnel management, internal meetings are held to promote the Company's core values of ethics and integrity. Through the formulation of a series of regulations, imple mentation of a self-review system, and establishment of a whistleblowing channel and whistleblower protection mechanism, we have created a comprehensive legal compliance firewall. The management leads by example, demanding our colleagues to make sure that their business conducts comply with the law or the Company's policies and internal regulations. The compliance status is examined through annual review meetings, and compliance guidelines are formulated for our colleagues, demanding them to comply with the "Human Rights Policy of CORUM and CORUM Ethical Corporate Management Best Practice Principles", irrespective of their position, rank, and location. The content includes work environment guidelines, equal opportunity, confidentiality clause, prohibition of part-time work, avoidance of conflicts of interest, prohibition of giving or receiving gifts, and compliance with business etiquette. Improve our corporate image through measures such as respecting employees and customers, whistleblower protection and immunity, etc. to ensure the Company's sustainable management and development. To prevent the Company from being punished for violating fair competition and antitrust laws, we have especially stipulated relevant codes of conduct, which should be complied with by the Company's management and employees while conducting business activities to lower the risk of breaking the law. The abovementioned measures were implemented for the sake of engaging in industrial compe tition by following the principle of integrity and fairness, thereby fostering a corporate culture of legal compliance and establishing a trustworthy, respected reputation for the Company.
(3) In terms of personnel training, to elevate our colleagues' professional ethics and legal compliance awareness, we have created internal regulations in accordance with the law, where the HR Department and other responsible departments work together to provide colleagues from different departments and ranks with relevant legal training. For instance, we provide colleagues with corresponding training based on their respective responsibilities including orientation training, physical courses, cross-unit promotion, and external training. Moreover,legal compliance guidelines are announced on posters in the Chiayi factory and on the Company website to allow our colleagues to stay in touch with the latest regulations at any time.
(4) Regarding occupational safety and health, Corum has introduced the ISO 14001 environmen tal management system and ISO 45001 occupational safety and health management system,and we have formulated the oversight, audit, and performance management regulations to ensure that the Company complies with environmental protection and occupational safety requirements during the product manufacturing process. Through an effective, circular operational environment and occupational safety management system, we can detect potential problems and take the appropriate management and preventive actions to protect the Company from damages.


Total Risk Management

planning and implementing risk manage-ment-related activities. Risk management encompasses corporate governance, environmental,and social aspects. Focusing on various responsible departments, we have launched relevant risk evaluation operations to ensure the Company's sustainability goals are achieved by evaluat-ing the risk probability and the level of its impact on the Company, as well as responding to specific high-risk items.
Currently, the material financial impact is defined by Corum's Finance Center based on calculations of four major types of financial risks:





COVID-19 pandemic prevention measures

Besides forming a pandemic prevention response team, Corum has also implemented the following:
1.Request various units to reinforce environmental cleaning and disinfection management.
2.Request the employees to wear masks, take body temperatures every day, and conduct self-health management. If abnormal health conditions are discovered, the Company will immediately try to understand, monitor the situation, and provide relevant assistance in pandemic prevention.
3.To minimize employee interaction, elevator traffic is diverted, and thebuilding's security door only allows people to leave, no entry is permitted. Visitors or people exhibiting abnormal health conditions are prohibited from entering the building.
4.Meetings or client visits are carried out online to decrease cluster infection.
5.Monitor the Central Epidemic Command Center's latest directives and respond swiftly.
6.Depending on the needs of various units, relevant computer files and reports are backed up by scanning, external hard drives, or flash drives so that colleagues working from home may continue their work and ensure normal business operation.
7.Various units form LINE groups, save cell phone numbers, emails, or other communication information, allowing personnel to contact at any time, thereby decreasing the risk of cross-infection due to contact.
8.Employees who must work from home for a certain reason or are quarantined at home should refer to the information management regulations if they need to connect to the Company's intranet via VPN.
Information Security Management

With the high level of development in the information age, the Company isvulnerable to unpredictable security risks while enjoying the benefits of conve-nience. In serious cases, the Company's information network and business may be interrupted, causing enormous damage to the Company and the stakeholders.The Company's highest-ranking executive is the IT executive, who is in charge of planning and promoting the information security measures of the headquarters and factories. An "information security team" is formed consisting of executives from IT and other units. It must engage in security prevention, crisis handling, and audit operations.
Information security policy
Abide by information security-related laws and provide adequate protection measures for the Company's information asset to ensure its confidentiality,integrity, and availability, acting as the highest guiding principle for the Compa-ny's information security management and operations.
● Regularly assess potential hazards' impact on the Company's information assets, formulate contingency and recovery plans for important information assets and key services. This is to make sure the ongoing operation of the Company.
● Encourage our employees to implement information security protection,establish relevant regulations and information security responsibilities,concepts, and conducts.
● Contractors, customers, or third-party personnel that have used or linked to the Company's information environment must adhere to the Company's information security policy and related regulations.
Information security management mechanism and solution
● User authorization management: The user must grant different authorizations according to different security levels.
● Operating system user authorization security management: Install the operating system in accordance with the Company's regulations and join the Company domain for centralized management. The operating system must receive regular security updates, while antivirus software must be installed on the Company's servers and computers. Furthermore, updates,scan engine, and virus codes are downloaded automatically every day. Measures for regularly renewing the user password.
● Application software security management: Besides installing the application software, tool software, and software suites needed for IT operations, installation of other special software requires separate applications and approval before it can be installed.
● Set up a screening mechanism for prohibited software and URLs in the firewall settings to deny access to prevent affecting network quality and security.
● Network communication security management: External VPN (remote) access and internal access (file transfer (FTP), instant messaging, special connection (HTTPS), and other network applications) must be reviewed by the information unit and approved by the executive in charge before access is granted.
● Application system security management: The information unit must restrict the access and update of the source code to authorized personnel, and set different program execution authorizations for different users based on the business needs.
● Backup management: System disaster recovery and database backup management-related measures are in place.
● Asset management: Conduct asset serial number management and regular inventory of equip- ment and personal computers in the data center.
● The online training method is applied to educate users on the security mechanism of operating system configuration and operation. The source and infection method of current viruses (Trojan horses, backdoors, worms, etc.) are explained to enhance the users' knowledge of security protection.
